Tor Network and Tor Browser
Hello there! Let me share a story – a journey into the world of internet privacy, a path that led me to discover the Tor network, the Tor Browser, and the fascinating SaveTor initiative. It’s a tale of digital awareness, a quest for anonymity, and a peek into the community’s efforts to safeguard our online world.

The Perplexing World of Online Privacy
My curiosity about online privacy started with a simple observation: ads popping up on my screen related to something I had just searched for. This led me to question, “How much of my online activity is actually private?” The more I dug, the more I found about the challenges of maintaining privacy online – from data tracking to government surveillance. It felt like a constant battle to keep my digital footprint hidden.
Understanding the Tor Network
What is the Tor Network?
The Tor Network, also known as The Onion Router, is a fascinating piece of technology that essentially gives you a cloak of invisibility when you’re browsing the internet. Imagine being able to walk through a crowded street without anyone recognizing you – that’s what Tor does for your online presence.
Download Tor Browser : https://www.torproject.org/download/
The Purpose of Tor
The primary goal of Tor is to protect your privacy and anonymity online. In a world where digital surveillance is rampant, Tor acts as a shield, hiding your identity, location, and online activities. It’s not just about avoiding prying eyes; it’s about maintaining freedom and safety on the internet, especially for those in oppressive regimes or for whistleblowers and journalists who need to share sensitive information securely.
However, Tor is not infallible. It has several drawbacks, including vulnerability to exit node eavesdropping, slower connection speeds due to traffic being relayed through multiple nodes, and restrictions by some websites and service providers. Poisoned nodes, operated by law enforcement agencies or hackers, can monitor Tor traffic for surveillance or espionage purposes. Still, the likelihood of being de-anonymized because of these poisoned nodes is relatively low
Historical Development by the United States Naval Research Laboratory
The story of Tor begins in the mid-1990s at the United States Naval Research Laboratory. The project was initially developed with the aim of protecting U.S. intelligence communications online. It was a time when the internet was growing rapidly, and the need for secure communication was becoming increasingly evident.
The Concept of Onion Routing
Onion routing, the core technology behind Tor, is quite ingenious. Here’s a simple way to understand it: Imagine sending a secret letter by putting it inside multiple envelopes, each addressed to different people in a chain. Each person in the chain only knows the next recipient and cannot see the original sender or the final destination. That’s how onion routing works.
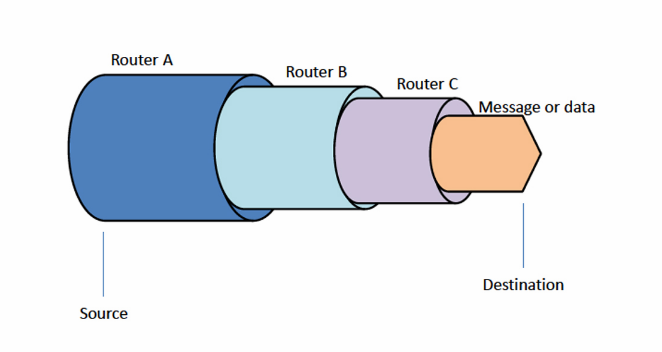
When you use Tor, your internet traffic is passed through multiple servers (or nodes), each peeling away a layer of encryption, just like the layers of an onion. This makes it incredibly difficult for anyone to trace your activity back to you. You get to your online destination without leaving a clear path behind.
This multi-layered approach is what gives Tor its strength in anonymous communication. Each relay in the Tor network only knows about its immediate predecessor and successor, but no single relay knows the complete path. Because of this, tracing the origin of the data becomes a complex puzzle, providing a strong degree of anonymity to the user.
Tor Network: Number of Active Servers and Bridges in 2023
As of 2023, the Tor network comprises a significant number of running relays and bridges, which are essential for its functioning. These servers are distributed across various countries and ISPs, contributing to the network’s diversity and resilience. The exact number of these servers can fluctuate over time, as it depends on the volunteers who run these relays and bridges. For the most current and detailed statistics on the number of servers in the Tor network, you can refer to Tor Metrics, which provides up-to-date information and graphs representing the network’s size and diversity.
How many users use Tor in 2023 ?
As of 2023, the Tor network, known for its focus on privacy and anonymity, has a significant user base. Over 2 million users access the Tor platform daily. This large number of users makes the Tor network one of the most popular networks offering anonymity to its users. The user statistics indicate that a substantial portion of Tor traffic is for regular internet activities rather than solely for accessing the dark web or engaging in illicit activities. In fact, visits to the dark web account for only about 1.5% of the entire Tor traffic.

Tor’s user base is distributed globally, with the largest share of mean daily users coming from Russia, which accounts for 22.47% of the total. The United States follows with 15.34% of the mean daily users. Other significant countries with a notable number of Tor users include Iran, Germany, Belarus, Brazil, India, the United Kingdom, China, and Turkey.
For more detailed information and the latest statistics, you can refer to Tor Metrics and TrueList’s Tor Stats 2023.
The Tor Browser – My Shield of Anonymity
As I delved deeper, I downloaded the Tor Browser, a pivotal element of this privacy-centric ecosystem. It was fascinating to see how it differed from conventional browsers. What intrigued me the most was how journalists and activists around the world used Tor to bypass censorship and share sensitive information securely. My explorations also led me to .onion sites, hidden services within the Tor network, offering an even deeper level of anonymity.

Fortifying My Online Fortress
Realizing the potential threats in the digital realm, I learned the importance of secure practices while using the Tor Browser. Opting for Linux over Windows was my first step, followed by disabling JavaScript for added security. I also made it a habit to regularly update the browser, understanding that staying ahead of potential vulnerabilities was key to safeguarding my online presence.
Facing the Challenges Head-On
Despite its strengths, Tor wasn’t without its challenges. I learned about issues like exit node eavesdropping, where the last relay in the Tor network could potentially expose user data. The trade-off between anonymity and connection speed was also noticeable, but for the sake of privacy, it was a compromise I was willing to make.
Lending a Hand to SaveTor.network
In my journey, I came across SaveTor.network, a beacon of hope for the Tor community facing DDoS attacks. This crowdfunding initiative aimed to bolster the Tor network by setting up new relays. Learning about their transparent donation process and real-time impact on the network, I felt compelled to contribute.
The website “Save the Onion Router” (SaveTor) is a crowdfund initiative aimed at improving the Tor network, which has been experiencing a heavy DDoS attack impacting its performance. The campaign, led by Riccardo Masutti, a Bitcoin researcher and InfoSec at Bitfinex, seeks to raise funds to set up new guard/middle Tor relays. It allows donations in Bitcoin and offers transparency through Bitcoin and BTCPayServer, showing real-time donations and newly configured relays. The project selects hosting services based on Bitcoin payment acceptance, privacy orientation, and sufficient technical specifications. Donors can choose specific nodes to launch or make arbitrary donations, which are used to launch new nodes and manage them for a year.
Supporting the Tor Project: A Vital Contribution to Online Privacy
In today’s digital age, the importance of online privacy and secure communication has never been more significant. The Tor Project, a non-profit organization dedicated to protecting internet users’ privacy and freedom, is at the forefront of this battle. By donating to the Tor Project, you’re contributing to a global effort to maintain and expand a network that safeguards individual liberty on the internet.
One of the most impactful ways to support the Tor Project is by funding Tor nodes with Bitcoin. This cryptocurrency donation not only embraces the ethos of decentralized, secure transactions but also directly contributes to the robustness of the Tor network. Your Bitcoin donations are used to maintain existing nodes and establish new ones, enhancing the network’s resilience and speed.
Moreover, the Tor Project has held fundraisers to add more relays to its network. Each relay added increases the network’s capacity, making it faster and more reliable for users worldwide. These fundraisers are critical in expanding the Tor network’s infrastructure, ensuring it remains a formidable tool against surveillance and censorship.
In summary, donating to the Tor Project, especially through Bitcoin, is more than a financial contribution. It’s a stand for online freedom, a step towards a more private and secure internet for everyone.
Tor Meets Cryptocurrency
My exploration didn’t stop there. I ventured into the realm where Tor intersects with cryptocurrency, providing an additional layer of privacy for transactions. The synergy between Tor and privacy-focused cryptocurrencies like Monero and Zcash opened my eyes to the vast potential of combining these technologies for enhanced digital security.
Conclusion
Reflecting on my journey, I’ve come to realize the vital role of tools like Tor and community-driven initiatives like SaveTor.network in our collective quest for digital privacy. It’s a testament to the power of community and technology in defending our right to an uncensored and private online experience.